If you're building a business around prepaid card issuing, payouts, or rewards programs, PCI DSS compliance isn't just a technical requirement—it's the mandatory security standard that makes your entire operation possible. Think of it as the universal rulebook for protecting sensitive payment data from fraud and data breaches.
Essentially, any company that processes, stores, or transmits cardholder details must maintain a secure environment according to these standards. For businesses launching white-label prepaid card programs, understanding this is step one.
The Blueprint for Payment Security
Imagine you're tasked with building a digital fortress to guard your customers' most valuable financial data. The Payment Card Industry Data Security Standard (PCI DSS) is your master blueprint for that fortress. It's not just a dry technical document; it's a living commitment to safeguarding every single transaction your business handles, from a simple payout to a complex rewards system.
This standard didn’t just appear out of nowhere. It was created by the major card brands—Visa, Mastercard, American Express, and others—to create a unified security protocol for everyone. They came together to form the PCI Security Standards Council (PCI SSC), an independent body that manages and evolves these standards to keep up with new and emerging threats.
More Than Just a Technical Audit
Here's what a lot of people miss: PCI DSS compliance is an ongoing process, not a one-and-done checklist you tick off once a year. It demands a constant, active dedication to security practices that protect your business, your customers, and ultimately, your reputation. For any company launching a prepaid card program for rewards or payouts, this commitment is the absolute foundation for building user trust.
The framework is always being updated to tackle the latest threats. For example, the latest major update, PCI DSS 4.0, rolled out 64 new requirements designed to seriously strengthen security measures. These changes push for better encryption, more robust vulnerability scanning, and mandatory multi-factor authentication (MFA) for any access to sensitive data environments.
The big shift here is from simple annual checks to proactive, real-time risk analysis. It’s a direct response to how fast cybersecurity threats change. You can dive deeper into these evolving standards and what they mean for businesses by checking out insights about PCI DSS 4.0.
At its core, PCI DSS is designed to create a secure environment wherever cardholder data is handled. This significantly reduces the risk of data breaches that can lead to catastrophic financial losses and irreversible damage to customer trust.
Why It Matters for Modern Payouts and Rewards
For businesses using APIs to issue white-label prepaid cards—like those enabled by a developer-first platform like Swype—PCI DSS compliance is the bedrock of the entire service. It’s the very thing that allows developers to build seamless payout and incentive programs without having to construct their own security fortress from the ground up.
When you partner with a compliant card issuing platform, you inherit a secure, pre-built foundation. This frees you up to focus on creating a fantastic user experience for your rewards or payout program, all while knowing every transaction is shielded by industry-leading security standards.
Deconstructing the 12 PCI DSS Requirements
To really get a handle on PCI DSS compliance, you have to understand the 12 core requirements that make up the standard. But don't worry, this isn't some dry, technical checklist. It's much easier to think of them as being grouped into logical security goals—the specific, actionable steps every business needs to take to build and maintain that digital fortress we talked about earlier.
Think of these 12 rules as the detailed instructions in your security blueprint. They cover everything from the ground up: how you build your network, how you manage who gets access, and how you keep an eye on things. It's this layered approach that makes PCI DSS such a tough nut for criminals to crack.
Goal 1: Build and Maintain a Secure Network
The first couple of requirements are all about setting up a strong perimeter for your payment environment. This is your first line of defense, designed to keep bad actors out from the very start.
-
Requirement 1: Install and Maintain a Firewall Configuration. Your firewall is basically the digital bouncer for your network. It stands at the door, checking the "ID" of all incoming and outgoing traffic to make sure only legitimate data gets through. A well-configured firewall stops attackers before they can even get a foot in the door.
-
Requirement 2: Do Not Use Vendor-Supplied Defaults. When you buy new network gear like routers or servers, they almost always come with default passwords like "admin" or "password." Requirement 2 says you have to change these immediately. Leaving them as-is is like leaving the key to your fortress under the welcome mat—it's one of the first things an attacker will try.
Goal 2: Protect Cardholder Data
Once your network perimeter is solid, the next job is to protect the data itself. These next two requirements are all about making the data completely unreadable and useless to anyone who shouldn't have it.
PCI DSS Requirement 3 is all about encryption, which is like a secret code for payment data. Even if an attacker somehow gets past your defenses and steals the data, encryption makes sure they can't actually read or use it without the unique decryption key.
-
Requirement 3: Protect Stored Cardholder Data. This rule is laser-focused on making any stored data useless to thieves. It demands strong encryption and other tricks to mask card numbers, like only showing the last four digits. For a card-issuing platform like Swype, this is absolutely fundamental to how we secure every single virtual card we issue.
-
Requirement 4: Encrypt Transmission of Cardholder Data. Data is at its most vulnerable when it's on the move across open, public networks like the internet. This requirement makes sure that any time cardholder data is sent from one place to another, it's wrapped in powerful encryption. It turns the data into a secure, private message that can't be snooped on.
Goal 3: Maintain a Vulnerability Management Program
A system that's secure today might have a glaring hole in it tomorrow. This group of requirements is all about staying one step ahead of threats by constantly updating and testing your systems.
-
Requirement 5: Protect All Systems Against Malware. This is your digital immune system. It means using and regularly updating anti-virus and anti-malware software to constantly scan for and neutralize known threats before they can cause damage.
-
Requirement 6: Develop and Maintain Secure Systems and Applications. Security can't be an afterthought; it has to be baked into your software from day one. This involves patching vulnerabilities the moment they’re discovered and sticking to secure coding practices to ensure there are no hidden backdoors for attackers to sneak through.
Goal 4: Implement Strong Access Control Measures
Technology is only half the battle. Security is also about people. These requirements make sure that only the right people can access the right information, and nothing more.
-
Requirement 7: Restrict Access to Cardholder Data by Business Need-to-Know. This is what we call the "principle of least privilege." Someone working in marketing has no reason to see payment data, so their access should be completely blocked. It's a simple idea that dramatically limits the potential for both accidental and malicious data leaks.
-
Requirement 8: Identify and Authenticate Access. Every single person who touches your systems needs a unique ID and a strong password (or another authentication method). This creates a crystal-clear audit trail, showing exactly who did what and when.
-
Requirement 9: Restrict Physical Access. This rule brings security out of the digital world and into the physical one. Any servers or hardware holding cardholder data must be kept in a secure, locked location with tightly controlled access. No exceptions.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you don't watch. This set of rules is about keeping a constant, vigilant eye on your security systems so you can spot and react to threats in real-time.
-
Requirement 10: Track and Monitor All Access to Network Resources and Cardholder Data. This means keeping detailed logs of all activity on your network. If a breach ever does happen, these logs are absolutely vital for figuring out how it happened and making sure it never happens again.
-
Requirement 11: Regularly Test Security Systems and Processes. You have to constantly poke and prod at your own defenses. This includes running things like vulnerability scans and penetration tests to find and fix weak spots before criminals can exploit them.
Goal 6: Maintain an Information Security Policy
Finally, a strong security posture needs a formal, written policy that guides the entire organization from top to bottom.
- Requirement 12: Maintain a Policy that Addresses Information Security for All Personnel. This last requirement ties everything else together. It mandates having a formal, documented security policy that everyone in the company understands and follows. This ensures everyone is on the same page and committed to protecting payment data.
How PCI Compliance Powers Modern Card Programs
Knowing the 12 requirements of PCI DSS is one thing. Figuring out how they actually apply to a modern payments platform is something else entirely. For businesses trying to launch a prepaid card program—whether for rewards, incentives, or customer payouts—that list of rules can look like a mountain. It’s a huge distraction, pulling critical resources away from what really matters: building a great product and user experience.
This is exactly where developer-first card issuing platforms completely change the game.
Instead of trying to build a secure payment system from the ground up, you can partner with a platform that has already done all the heavy lifting. Modern card issuing platforms like Swype are built with PCI DSS compliance baked into their DNA. Security isn’t just an add-on; it’s woven directly into the API-driven infrastructure that fuels every single transaction.
The API-First Advantage in Security
An API-first approach means security is handled at the foundation, not patched on later. When you use a developer-first platform like Swype to issue white-label prepaid cards, you’re plugging into a ready-made, pre-certified Cardholder Data Environment (CDE) via simple APIs.
This model takes a massive amount of risk off your plate. Forget about managing your own secure servers, encrypting data, and bracing for painful annual audits. You get to offload the most complex and sensitive parts of PCI DSS compliance. Your team is then free to focus on what they do best, whether that's designing a slick payout experience for employees or a fun rewards program for customers, all with the confidence that the security is rock-solid.
This infographic breaks down the difference between building a card program in-house versus using a PCI-ready API platform.
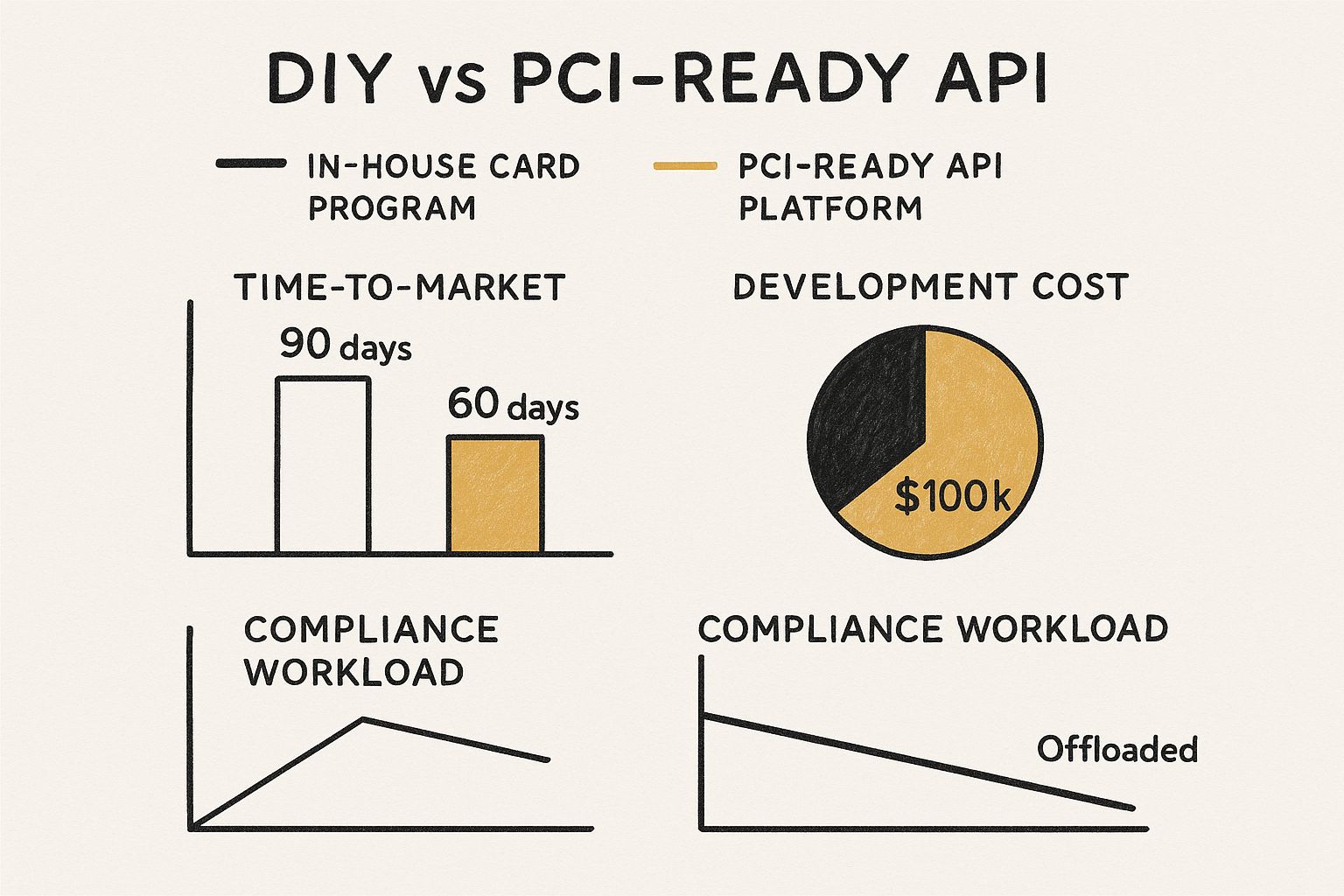
As you can see, partnering with a compliant platform doesn't just get you to market faster—it slashes the development costs and internal workload tied to security and governance.
Focusing on Growth, Not Governance
This shift in responsibility couldn't be more important in today's market. The demand for secure, compliant payment solutions is exploding. The PCI Compliance Services Market was valued at roughly USD 1.32 billion in 2023 and is on track to more than double to about USD 2.65 billion by 2030. This growth is a clear signal: businesses that prioritize secure payment tech will be the ones that earn trust and stay competitive. You can get more details on the growth of the PCI compliance market here.
By integrating with a PCI-compliant card issuing API, businesses effectively shrink their own PCI scope. This means fewer requirements to juggle, simpler audits, and a much faster path to launching a secure and reliable card program.
At the end of the day, this approach lets you innovate without having to become a security expert. It changes the conversation from, "How on earth do we become PCI compliant?" to "How can we build the best possible card program for our users?" That freedom to obsess over the customer experience—whether for instant payouts or loyalty rewards—is the real power of building on a secure, compliant foundation.
Finding Your PCI DSS Compliance Level
So, what does PCI DSS compliance actually look like for your business? It starts with a pretty straightforward question: how many card transactions are you processing?
Compliance isn’t a one-size-fits-all jacket. The rules scale based on your transaction volume, making sure the security measures match the level of risk you carry. Think of it this way: a small business launching its first employee incentive program with a handful of prepaid cards has a much different—and simpler—path to compliance than a massive corporation handling millions of payouts.
Figuring out your level is the first, most critical step. It tells you exactly what you need to do to prove you’re secure.
The Four Levels of Compliance
While the major card brands like Visa and Mastercard have their own specific thresholds, they all follow the same basic tiered structure. The more transactions you process, the more intense the validation process gets. This makes perfect sense—the biggest processors are the biggest targets for attackers, so they’re held to the highest possible standard.
For most businesses just getting started, especially those launching a new white-label card program through a platform like Swype, you'll almost certainly fall into a lower tier. This is good news. It means your validation process will be far more manageable, usually involving a self-guided questionnaire instead of a pricey on-site audit.
The core idea is simple: your compliance journey is directly tied to the scale of your payment operations. The more cardholder data you handle, the more you need to demonstrate that your security is ironclad.
What is Required at Each Level?
The real difference between the levels boils down to the validation method. At the lower levels, you can self-certify that you're compliant. But as you move up the ladder, you'll need an independent security professional to verify everything for you.
Here are the two main ways this happens:
-
Self-Assessment Questionnaire (SAQ): This is essentially a checklist you complete yourself to report your compliance. There are different versions of the SAQ depending on exactly how you handle payments, but it’s the standard for businesses with lower transaction volumes.
-
Report on Compliance (ROC): This is the big one. It's a formal, detailed report generated from an on-site audit conducted by a Qualified Security Assessor (QSA). This deep dive is mandatory for Level 1 organizations—those with the highest transaction volumes—to prove they meet every single PCI DSS requirement.
To help you see where your business might fit, we’ve put together a quick comparison of the four levels.
PCI DSS Compliance Levels at a Glance
This table breaks down the typical transaction volumes and what's required to validate your compliance at each level.
| Compliance Level | Annual Transaction Volume (Per Card Brand) | Required Validation |
|---|---|---|
| Level 1 | Over 6 million transactions | Annual Report on Compliance (ROC) by a Qualified Security Assessor (QSA) |
| Level 2 | 1 million to 6 million transactions | Annual Self-Assessment Questionnaire (SAQ) and quarterly network scans |
| Level 3 | 20,000 to 1 million e-commerce transactions | Annual Self-Assessment Questionnaire (SAQ) and quarterly network scans |
| Level 4 | Fewer than 20,000 e-commerce transactions | Annual Self-Assessment Questionnaire (SAQ) recommended; may vary by acquirer |
Note: These thresholds are general guidelines. Always confirm the specific requirements with your acquiring bank and the card brands you work with.
Pinpointing your level clarifies your next steps, turning a complex set of rules into a clear, actionable plan.
The Real Business Cost of Non-Compliance
It's tempting to think of PCI DSS compliance as just another box to check, maybe even a corner you can cut to save time and money. But treating it that way is a high-stakes gamble you can't afford to lose. The real question isn't about the rules themselves, but what actually happens when you ignore them. The fallout is real, it’s severe, and it can send shockwaves through your entire business.
We're talking about everything from your bank balance to the trust you've built with your customers.
The most immediate hit comes from financial penalties. And these aren't just slaps on the wrist; they're significant, recurring fines that can drain your resources month after month.
The Direct Financial Penalties
The acquiring banks—the ones that process card payments for you—are the first to come knocking. They can levy steep monthly fines for non-compliance. On top of that, they might hike up your transaction fees, slowly and silently eating away at your profit margins.
Just how crippling are these costs? Fines for non-compliance often run anywhere from $5,000 to $100,000 per month. The exact amount depends on your business size and just how badly you’ve dropped the ball. When you remember that data breaches hit roughly 1.35 billion people across the globe in 2024 alone, the risk starts to look terrifyingly real. For a deeper dive into these risks, check out these insights on PCI DSS compliance.
Beyond the Fines: The Long-Term Damage
As painful as those fines are, the long-term damage to your reputation can be far more devastating. A single data breach stemming from non-compliance can vaporize the customer trust you've spent years building.
In the world of payouts, rewards, and prepaid card programs, trust is everything. A security failure tells customers that their sensitive financial data is not safe with you, and that’s a reputation that is incredibly difficult to repair.
This loss of trust leads straight to customer churn. Once your name is tied to a breach, people will think twice before using your white-label card programs or payout services. Your competitors who do take security seriously will be waiting with open arms.
Ultimately, seeing PCI DSS compliance as just a regulatory chore is a massive misstep. Think of it as a fundamental investment in your company’s stability, security, and future. For a developer-first, API-driven platform like Swype, compliance isn't just a feature—it's the bedrock promise of security for every partner and end-user. It's what protects the business, secures customer data, and ensures your card programs are built to last.
Common Questions About PCI DSS Compliance
When you're launching a prepaid card program, questions about PCI DSS compliance are bound to come up. It's a complex topic, and a lot of myths and misconceptions float around. Let's clear the air and tackle some of the most common questions businesses ask.
These aren't just academic exercises—they're the real-world hurdles you'll face.
If I Use a Third-Party Processor, Am I Automatically Compliant?
No, and this is probably the single biggest misunderstanding about PCI DSS. Using a compliant card issuing partner like Swype dramatically shrinks your compliance burden, but it doesn't eliminate it entirely.
Think of it as a shared responsibility. Your partner handles the heavy lifting—securing the actual cardholder data environment (CDE)—but you're still responsible for your end of the chain. You need to make sure your own systems and processes are secure. This usually means you'll still need to complete a Self-Assessment Questionnaire (SAQ) to confirm you're holding up your end of the bargain. The bottom line is your business is ultimately responsible for ensuring the entire payment data flow is locked down.
Does PCI DSS Apply if My Business Doesn't Store Card Data?
Yes, it almost certainly does. PCI DSS isn't just about storing card numbers; it covers the entire lifecycle of cardholder data. That includes any system that processes or transmits that information, even for a split second.
So, even if you never save a card number to a database, the standard still applies to the systems that see the data as it passes through. This could be your website's checkout form, a point-of-sale terminal, or the APIs that connect to your payout platform. While your compliance workload will be much simpler (often a shorter SAQ), you aren't off the hook.
PCI DSS compliance isn't just about storage; it's about protecting data at every single touchpoint. Any system that "sees" the data, even for a moment, falls within its scope.
Is PCI DSS Compliance a One-Time Thing?
Absolutely not. This is a critical point: PCI DSS compliance is an ongoing commitment, not a one-and-done project you can check off a list. The threat landscape is always shifting, with new vulnerabilities discovered all the time. Your security has to keep up.
Staying compliant means continuous effort. This involves things like running quarterly vulnerability scans, constantly monitoring your security controls, and completing an annual validation to prove your defenses are still strong. It’s a year-round job that protects both your customers and your business.
What's the Difference Between a QSA and an ASV?
Both a Qualified Security Assessor (QSA) and an Approved Scanning Vendor (ASV) are certified by the PCI Security Standards Council, but they have very different jobs.
-
Qualified Security Assessor (QSA): Think of a QSA as a full-blown auditor. They are certified companies that conduct formal, on-site PCI DSS assessments and produce a detailed Report on Compliance (ROC). This is typically required for Level 1 merchants—the big players with the highest transaction volumes.
-
Approved Scanning Vendor (ASV): An ASV is a certified company that performs the required quarterly external vulnerability scans on your network. These automated scans are like a security patrol, checking your systems for any obvious holes from the outside. These scans are a must for nearly every merchant and service provider, no matter their size.
Ready to launch a secure, global prepaid card program without the compliance headache? With Swype, you can issue virtual Visa and Mastercard cards for rewards, incentives, and payouts through a simple, developer-first API, all built on a PCI DSS compliant foundation.
Start building your white-label card program with Swype today.
